Sniff WiFi traffic with LessLinux
LessLinux is used as a foundation for quite some security and forensic distributions. Thus more features for analyzing network traffic get added. Recent builds include “hostapd” and “brctl” for creating ad-hoc hotspots that can be used to monitor the traffic of selected WiFi enabled devices like smart TVs or smartphones. I usually use a notebook with a wired and a wireless interface for this task.
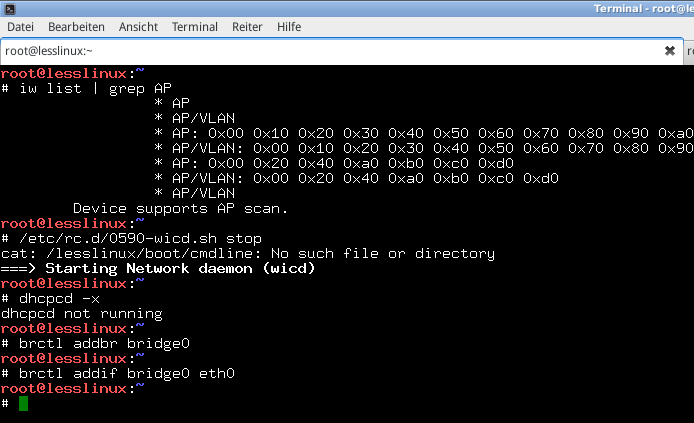
To create such a bridged access point a WiFi interface that supports master (or access point) mode must be present – grepping for AP in the capabilities list will identify matching chipsets. Some interfaces like those sold by Realtek only offer the possibility to create unencrypted access points with the vanilla hostapd. In this case you may want to try USB wifi devices.
Download latest build: lesslinux-search-and-rescue-uluru-20160226-111022.iso
First, shut down wicd and dhcpcd:
/etc/rc.d/0590-wicd.sh stop
dhcpcd -x
…and add a bridge device that is linked to the ethernet interface:
brctl addbr bridge0
brctl addif bridge0 eth0
Now create a configuration file /etc/hostapd.conf:
interface=wlan0
ssid=LessLinux
hw_mode=g
channel=11
wpa=2
wpa_passphrase=topsecret
wpa_key_mgmt=WPA-PSK WPA-PSK-SHA256 WPA-EAP WPA-EAP-SHA256
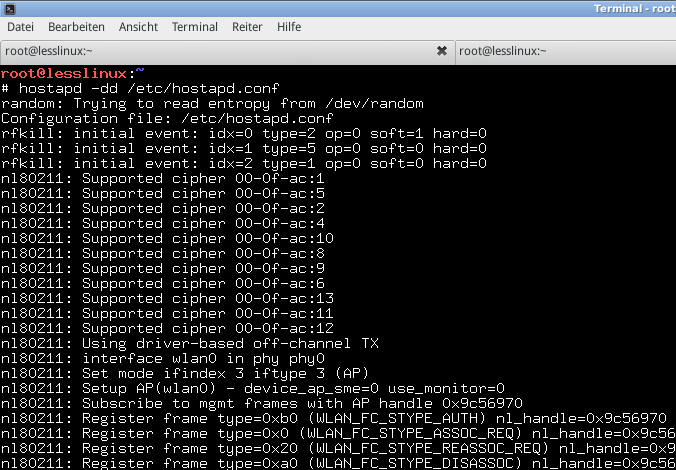
Use another terminal to start hostapd (with -dd it won’t fork to background):
hostapd -dd /etc/hostapd.conf
In the first terminal add the wireless interface to the bridge and enable all interfaces:
brctl addif bridge0 wlan0
ifconfig wlan0 up
ifconfig eth0 up
ifconfig bridge0 up
Bridging works now, but your computer itself did not yet acquire an IP address, usually you use dhcpcd to acquire one for the bridge interface:
dhcpcd -z bridge0
Now connect to the access point. If connection fails with an authentication failure, stop hostapd by pressing Ctrl+C and remove the lines beginning with “wpa*” from hostapd.conf to create an unencrypted AP (might be dangerous!) or try with different WiFi interfaces.
When the connection is established, you might want to use tcpdump to capture traffic for analyzing later or use wireshark for a live capture.